External Applications
Plugins require a set of credentials to be configured as an external application in the Banno People app.
The back office administrator at your financial institution can do this for you in the External applications section of Banno People.
If you are a financial institution or working directly with a financial institution, you should work with the back office administrator at your institution to get appropriate access to Banno People.
If you are a fintech or other developer working without a financial institution, you are likely using the JackHenry.Dev developer portal. In this case, you will not have access to Banno People, however you will still have the ability to create and configure many aspects of your external application and plugin.
For more information on this, see our troubleshooting page.
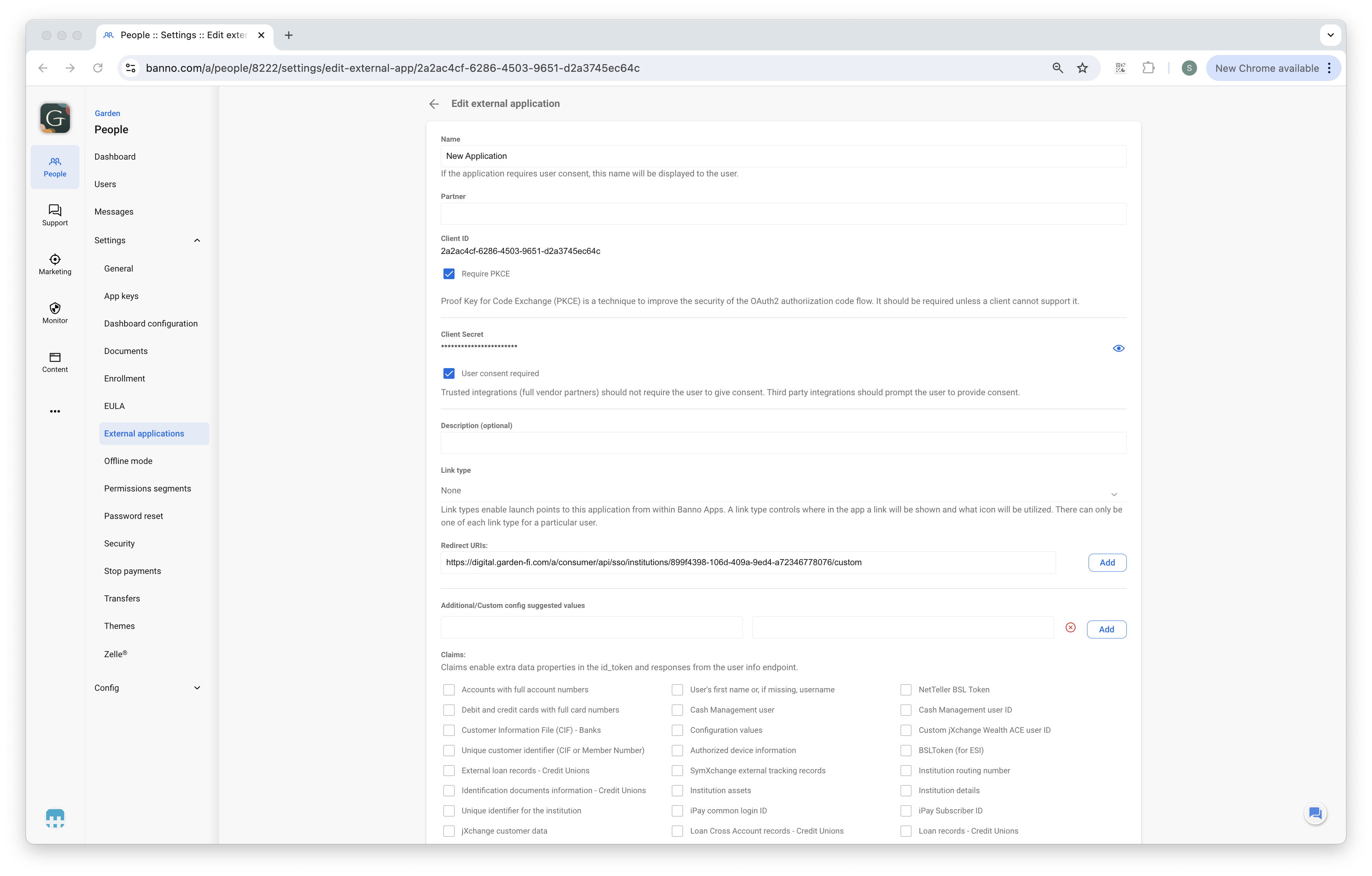
First, the administrator must select Custom name as the type of external application. They will need to enter a name for these credentials.
Next, the administrator must select a Link type of PluginCard. They will need to enter a name for the Link title.
Finally, the administrator must enter your Redirect URI and click the save button. The Redirect URI (and the auto-generated Client ID and Client Secret) are what you’ll use to authenticate with Banno using OAuth/OpenID Connect. See the Authentication topic for more details.
The External Application is what you’ll use when configuring your plugin.
User type filter
It’s possible to designate what types of user have access to an external application. By default, all external applications are set to All user types, however, you can also choose to configure your external application to only Retail or Cash Management.
Additionally, if you do designate a specific user type, you can still override the configuration for specific users.
Order of redirect URIs
It is possible to add more than one redirect URI. However, the order is important.
- The redirect URI that handles the initial authentication flow for your plugin must appear first in the Redirect URI list since Banno’s Dashboard UI expects to call the first redirect URI to render the plugin’s card face.
- The order is not important for any other redirect URIs in the list.
Exact string matching of redirect URIs
Each redirect URI is matched using exact string matching. If the redirect URI does not match, then the authorization flow will not be valid.
- Redirect URI matching is case-sensitive and path-inclusive.
- For example,
http://localhost:8080/dynamicis NOT the same ashttp://localhost:8080/Dynamicsince the first uses a lowercase “d” and the second uses an uppercase “D”. - Similarly,
http://localhost:8080/dynamicis NOT the same ashttp://localhost:8080/dynamic/since the second ends with a slash while the first does not.
- For example,
- ‘Wild card’ redirect URI formats are not allowed, so
https://*.example.comis NOT valid.
Dynamically updating Content Security Policy (CSP) with redirect URIs
See the Restrictions page for more details.